Challenges Facing the Security of the Software Supply Chain
Paolo Mainardi | 05 October 2023
Introduction
In today's rapidly evolving technological landscape, secure software development, especially in the FOSS ecosystem, has become a crucial aspect of the software supply chain.
Open source is becoming the de facto standard for building new software or evolving existing ones; it is estimated that at least 90% of organizations are adopting it at scale. Even if the industry knows the best practices for consuming open source software, it is still happening that software from anonymous contributors gets integrated or updated without proper diligence. This is not an issue of the OSS model per se, but it is amplified because the number of external dependencies in this model could be very high.
Supply chain attacks occur when an attacker targets a vulnerability in a third-party vendor's software at any point in the chain, a phenomenon which has become more frequent and sophisticated. This phenomenon is also helped, in some ways, by the absence of awareness of the threats and risks associated with OSS vulnerabilities. Take for example the Log4j download dashboard from Sonatype, which clearly shows how software developers are still consuming hundreds of thosands of vulnerable versions of Log4j.
Here is what a modern software supply chain looks like today and where threats may hide at any point:
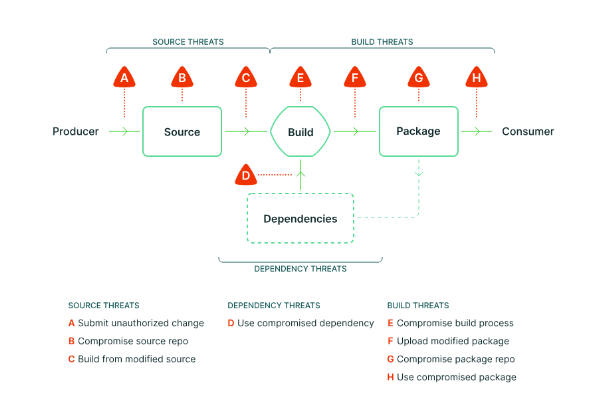
Image: Illustration of a modern software supply chain. Credits: https://slsa.dev/spec/v1.0/threats-overview
This blog post will examine the current state of secure software supply chains, including the challenges and solutions associated with securing the software supply chain and how the community is working to address the issues in several directions.
The importance of secure software supply chains
The software supply chain is developing, delivering, and maintaining software, often involving multiple vendors and third-party components, such as third-party dependencies, CI/CD systems, build and artifact repositories, cloud vendors, and, last but not least, local or cloud development environments, that more and more subject of attacks, like the recent discovery of VSCode malicious extensions crafted to steal sensitive data masquerading themselves as legitimate extensions, using typo-squatting as an attack technique.
It is worth mentioning that, regarding the last point, Aquasec tried to reproduce this kind of attack with a simple POC by creating a package that masqueraded as Prettier, one of the top ten most installed extensions in the Marketplace. The package sent a ping each time it was installed. The result was that in just 48 hours, they got a thousand installs from around the world. This demonstrated how easy it could be for a real attacker to create a malicious extension at a large scale with relatively low effort. This is critical because the development environment is where sensitive data lives, like cloud credentials, that, once stolen, can lead to attacks like the one unleashed on LastPass in 2022.
So, a secure software supply chain is essential for organizations to protect their customers' data and their intellectual property.; A secure software supply chain also helps minimize the risk of data breaches, which can be costly and damaging to an organization's reputation.
Nowadays, we are aware that cyber attacks on software supply chains, such as the SolarWinds incident, can even pose a threat to national security. This case served as a wake-up call for everyone, including governments.
In response, new cybersecurity laws and actions have been proposed or implemented to regulate the software supply chain and improve OSS security to mitigate emerging threats.
This includes the National CyberSecurity strategy from the U.S. federal government, the Cyber Resilience Act (CRA) from the European Commission, and their connected initiatives and funds to nurture the ecosystem. The outcomes of these policy initiatives are not yet clear.
Other than governments, the community has responded strongly by creating the Open Source Security Foundation (OpenSSF), part of the Linux Foundation, a cross-industry forum for collaborative improvement of open source security by working upstream and with existing communities, working on projects like Sigstore and its public good infrastructure, the SLSA framework, the Secure Supply Chain Consumption Framework (S2C2F), OpenSSF Scorecard, RSTUF, the Alpha-Omega project, the training courses and much more. You, too, can get involved.
One of the latest initiatives that went public by OpenSSF was the Open Source Consumption Manifesto (OSCM), a set of common principles that organizations can adopt to achieve a real, measurable change in the security and health of their software supply chain.
This is a big step forward for the entire industry, citing the working group:
“The Open Source Consumption Manifesto (OSCM) aims to address the gaps mentioned above. But, it is also intended to be a living document. Our goal with the OSCM is to find common ground, to unite many different approaches. Like the Agile Manifesto, the OSCM embraces a set of core values. In partnership with those values are fifteen guiding principles.
Our hope and simple goal: improve open source consumption in every software organization.”
OSCM announcement post: https://openssf.org/blog/2023/08/24/join-us-in-adopting-the-open-source-consumption-manifesto/
Challenges in securing the software supply chain
Existing and emerging attacks are growing pace rapidly. In 2022 attacks increased by more than 742% according to the Sonatype State of Software Supply Chain report. There are several well-known types of attacks; the most common are:
- Dependency and namespace confusion
- Typosquatting and its cousin–Brandjacking
- Malicious code injections
- Protestware
All of them are affected by how the software is consumed and how much effort is spent by developers and organizations to conduct due diligence before integrating a new piece of software written by some anonymous or pseudonymous contributors, even though there are in place several best practices as previously mentioned, OSS ecosystem suffers of seeing them applied at scale.
Just some weeks ago, another case was discovered by software supply chain security firm Phylum, where a highly targeted and sophisticated attack plagued NPM.
The company said that "due to the sophisticated nature of the attack and the small number of affected packages, we suspect this is another highly targeted attack, likely with a social engineering aspect involved to get targets to install these packages.” This is different to what we’ve previously seen with typo-squatting attacks that are designed to target as many users as possible.
Again citing the Phylum, this type of attack exhibits similar behaviors to a previous attack wave uncovered in June, which has since been linked to rogue state actors.
This attack completes a range of categories targeting narrow or broad objectives, posing threats to all OSS consumers. to rogue state actors.
As Dan Lorenc, Founder and CEO of Chainguard, says:
“This looks like it was a flood of low-quality malware designed to trick 1-2 people. I'm still constantly paranoid about a lower scale, more patient attack. Imagine a nefarious group spending 1-2 years with a small team of engineers, making useful software and publishing it under a permissive license on GitHub.
With a little skill and luck, and a few years of time you'd be able to get your software deployed incredibly broadly.”
One of the biggest challenges is the lack of visibility into the software supply chain. Many organizations rely on third-party vendors to provide software components, and they may not have full visibility into the security of those components. This lack of visibility makes it difficult for organizations to identify vulnerabilities in the software supply chain and take appropriate action to mitigate the risk.
This challenge is currently partially solvable by consuming, producing, and requiring a Software Bill of Materials (SBOM) for any piece of software consumed, which is also mandatory for U.S. agencies following President Biden's Cybersecurity Executive Order.
Even though the adoption is growing rapidly, nearly a quarter of large enterprises have not implemented SBOMs, as reported by the latest research, “Government intervention, the rise of SBOM and the evolution of software supply chain security” by Sonatype.
Simply having an SBOM is insufficient for securing the software supply chain.
However, it is an essential artifact for establishing software transparency and scanning for known vulnerabilities with tools like Trivy and Grype.
The topic of vulnerabilities is quite complicated, but Surendra Pathak, the CEO and Founder of Interlynk, did a great job of summarizing it in the article titled "VDR, VEX, OpenVEX and CSAF." which is a must-read to deep-dive into standards, technologies and ongoing challenges.
We are currently in the age of Generative AI, the next generation of artificial intelligence. Alongside this, the popularity of LLM machine learning models has rapidly increased, making them a key part of many new software and ecosystems. These models are now considered part of the software supply chain and should be treated with the same level of care to ensure integrity, transparency, and security.
That’s why OWASP has recently announced the release of version 1.5 of CycloneDX SBOM standard with the capability of describing machine-learning models through ML-BOM.
“ML-BOM represents a developer-friendly advancement in BOM technology. With ML-BOM, CycloneDX provides insights into the machine learning models utilized in software systems. This transparency allows stakeholders to understand and verify the training and deployment methods employed, ensuring accountability and promoting ethical artificial intelligence (AI) practices,” as it recites the OWASP announcement.
Although the standards and tools in the Generative AI ecosystem are rapidly evolving, many unanswered questions at all levels are not made of software, including politics, academia, industry, and regulators, making the future uncertain.
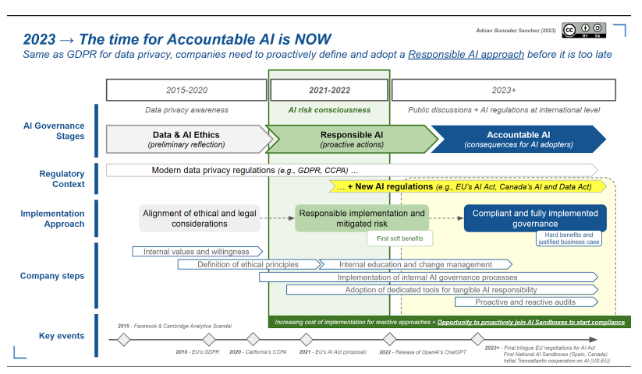
A recent article worth reading on this matter is "2023: The Time for Accountable AI is NOW" written by Adrián González Sánchez and Ofer Hermoni for the LF AI & Data Foundation who examines the recent progress and challenges in AI regulation, discussing the global drive toward formulating rules for responsible AI deployment. With a particular focus on the roles of both the open-source community.
Conclusion
In this post, we examined the challenges associated with the securing the software supply chain ecosystem, new initiatives, and responses to emerging trends, such as Generative AI becoming part of many software stacks. We also highlighted the important role of open source communities in addressing these issues.
This is just the beginning of a new awakening; as the OSCM manifesto says, at the end of 2021, everything changed after the SolarWinds and Log4shell cases, but the future is bright for open source with some big uncertainty as the Cyber Resiliency Act, which can have a huge impact for the European market and inadvertently risks imposing a major burden on open source contributors and non-profit foundations. The help of the broader community is needed to take immediate action.
As I conclude this article, I must mention a fascinating book titled "Securing the Software Supply Chain." It is authored by Michael Lieberman, the CTO and co-founder of Kusari, who is also a CNCF Security TAG lead, OpenSSF TAC member, a member of the SLSA steering committee, and co-authored by Brandon Lum, the ****Co-Chair of the CNCF Security TAG, and a part of Google's Open Source Security Team.